Image Steganography System
-
PorjectAcademic
-
Year2023
-
TypeCyber Security
-
Post
About
StegaX designed to enhance data security by concealing confidential information within images, adding an extra layer of protection against unauthorized access. This involves embedding secret messages within image pixels, making them invisible to the human eye.
Problematic
In an increasingly digital world, data security is paramount. Traditional methods of securing data may fall short, and that's where StegaX comes in. It provides a solution to the challenge of safeguarding sensitive information effectively.
Solution
StegaX is our innovative solution to the practice of image steganography, which involves concealing secret information within images to enhance data security. We have developed a user-friendly system that empowers users to securely embed confidential messages within images, making them imperceptible to the human eye.
Our solution uses the LSB (Least Significant Bit) algorithm for seamless message embedding while preserving the original image's visual integrity. Users can confidently protect sensitive information by utilizing StegaX's robust encryption methods.
User Flow:
1- Registration:
The user starts by registering an account on the StegaX platform, providing their username and a secure password.
Behind the scenes, StegaX employs robust security measures to validate and hash the user's password, ensuring data protection from the outset.
2- Logging In:
After successful registration, the user logs in to their StegaX account.
StegaX verifies the user's credentials securely before granting access.
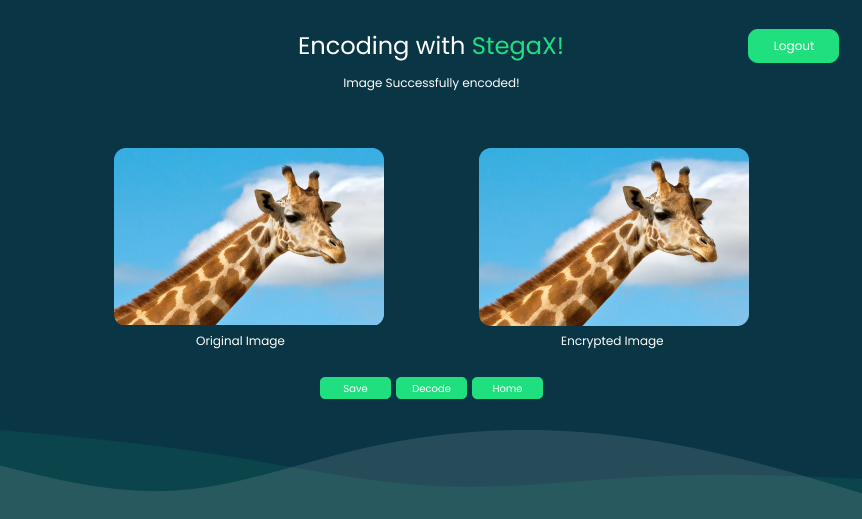
3- Encryption:
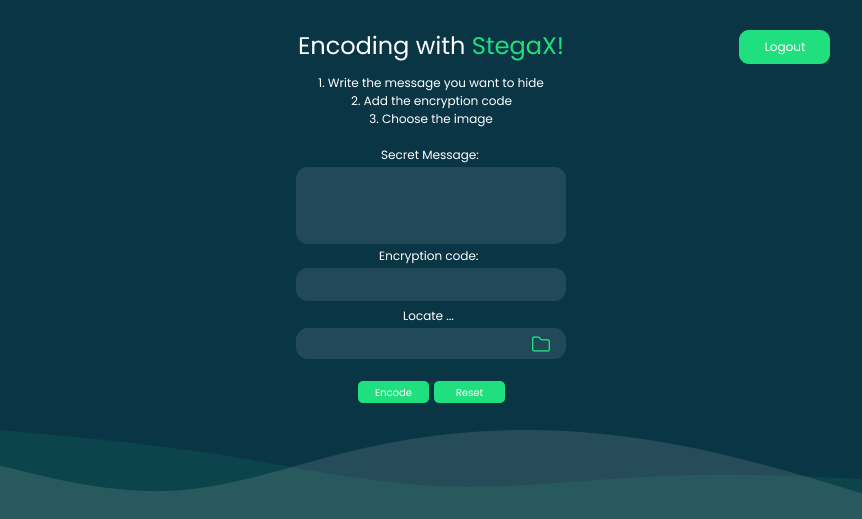
Once logged in, the user can choose the encoding option, he/she uploads an image that they want to use for steganography,
then enters the secret message they want to hide within the image.
StegaX utilizes encryption algorithms and the user's defined encryption key to secure the message.
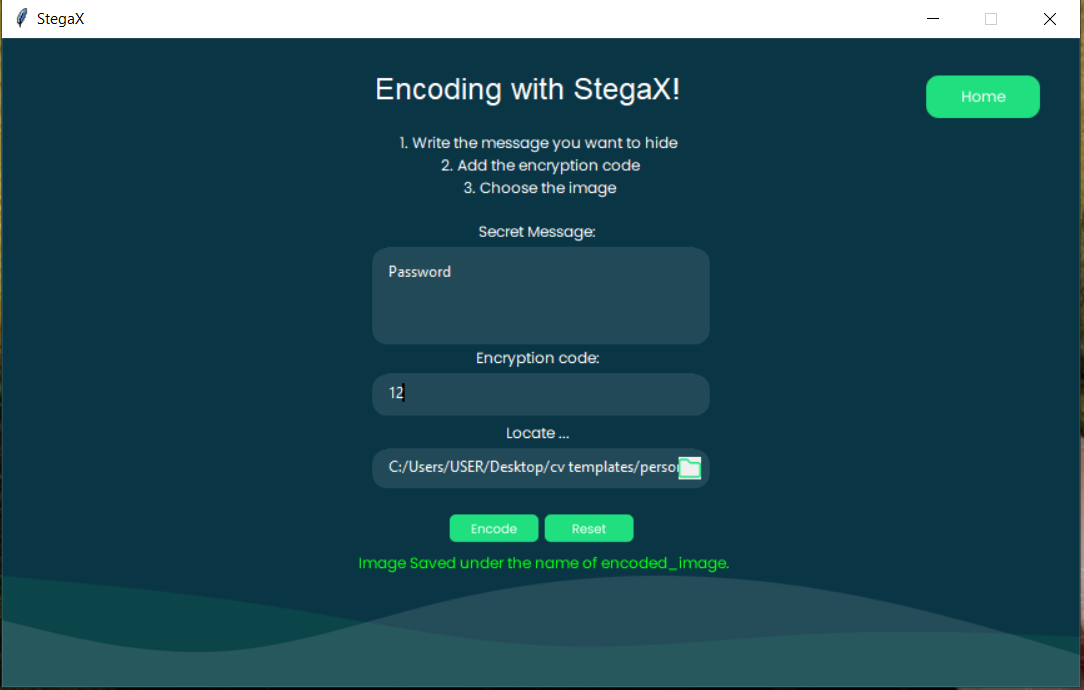
4- Embedding the Message:
StegaX employs the LSB (Least Significant Bit) algorithm to seamlessly embed the encrypted message within the image.
This process is imperceptible to the human eye, ensuring that the image's appearance remains unchanged.
5- Downloading the Encrypted Image:
The user can now download the modified image, which contains the hidden message.
StegaX ensures that the image is saved securely to the user's desktop.
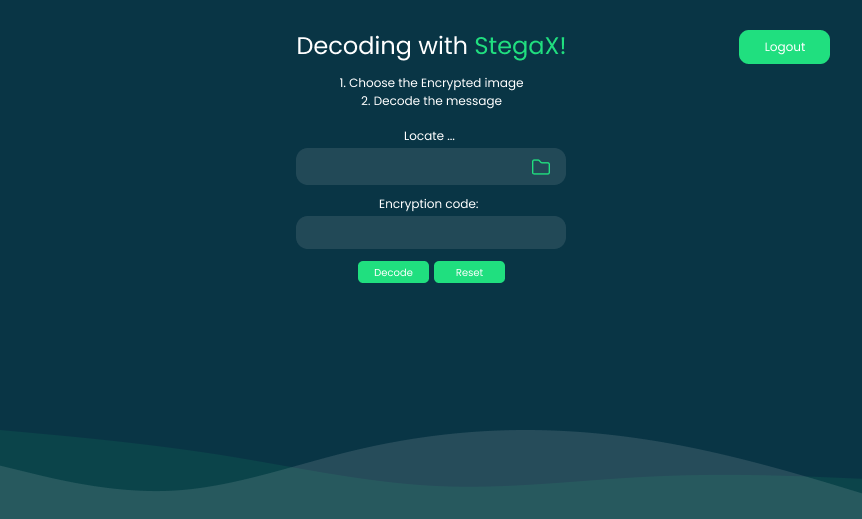
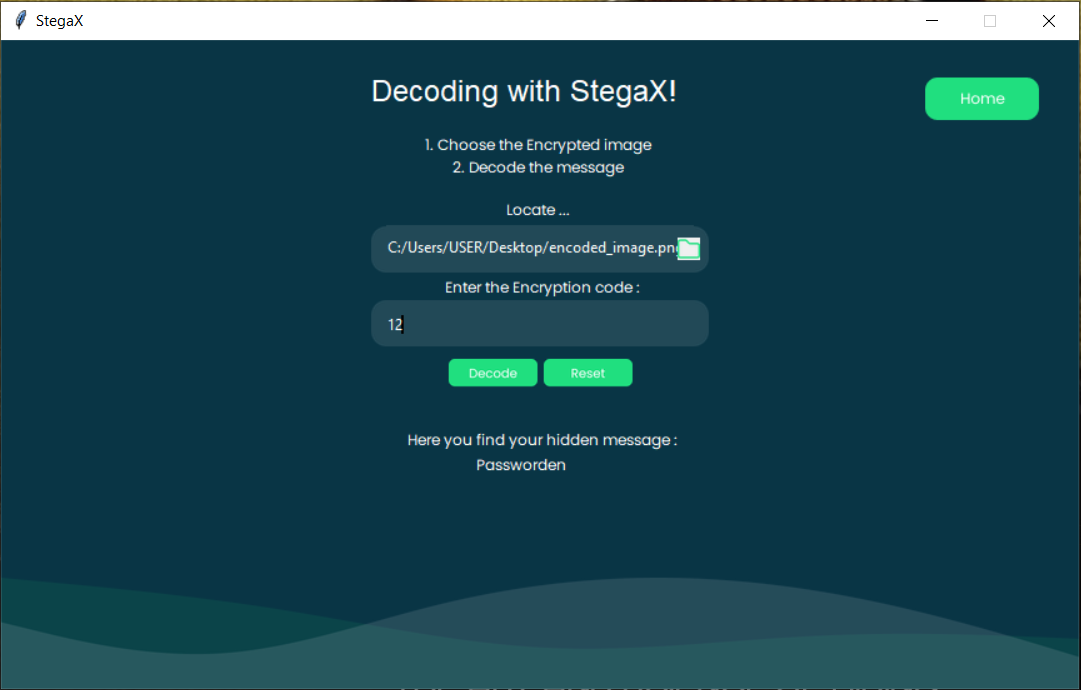
6- Decryption and Message Retrieval:
The user can send the image with whome concerned while sharing secretly the encryption key, so that the receiver can later upload the modified image to StegaX.
StegaX decrypts the hidden message using the user's encryption key, ensuring data confidentiality.
7- Logging Out:
After completing their tasks, the user can safely log out of their StegaX account.
StegaX ensures that the user's session is ended securely.
Key Achievements
✅ Robust Security: Strengthened password verification and secure password hashing in our database ensure the highest level of protection for user data.
✅ Encryption at its Best: We've implemented user-defined encryption keys and symmetric algorithms to encrypt and decrypt messages, providing an additional layer of security.
✅ Imperceptible Concealment: Our utilization of the LSB (Least Significant Bit) algorithm allows seamless hiding of secret messages within images without perceptible changes to the naked eye.
✅ Intuitive User Experience: Through our intuitive and aesthetically pleasing GUI developed using the Tkinter library in Python, users can effortlessly navigate and interact with StegaX.
Lessons Learned
The journey of developing StegaX has been a significant learning experience, contributing to my skills and knowledge in various domains:
•Technical Expertise: Extensive work with Python and exploration of libraries for image processing and cryptography has significantly enhanced my technical skills.
•Collaborative Excellence: Collaborating with an exceptional team has strengthened my teamwork and communication skills, fostering a collaborative and supportive environment.
•Agile Problem-Solving: Overcoming challenges during the development process has honed my problem-solving abilities and nurtured a creative mindset.